What Is the Best Identity Solution for Azure Virtual Desktop?
Azure Virtual Desktop uses the AD DS domain join feature for all session hosts, and the user must enter domain credentials to log in to Azure Virtual Desktop. To avoid a dependency on site-to-site VPN/ER for authentication traffic to on-premises AD DS, on-premises AD DS can be extended to the Azure hub subscription by creating a domain controller VM in Azure. Most organizations do not want to store password hashes in the cloud AD and prefer to go with pass-through authentication with on-premises AD. This approach increases traffic and dependency on the site-to-site VPN tunnel by sending all authentication/DNS traffic to the on-prem AD. Extending the AD domain controller to Azure is the recommended option if all application/services are using on-premises AD for authentication or else the Azure AD connect VM can be placed on-premises to sync on-premises AD users directly to Azure AD if you have fewer users using cloud services.
Figure 3-5 shows a reference architecture for on-premises AD sync with Azure AD for Azure Virtual Desktop auth.
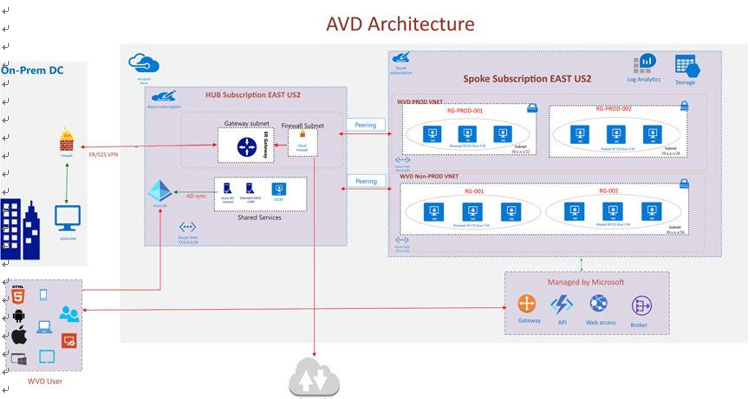
Figure 3-5. Azure Virtual Desktop identity solution
This diagram shows a typical architectural setup for Azure AD sync.
•\ All domain controller replication traffic flows over a site-to-site VPN/ER.
•\ A cloud-extended domain controller can be used for authentication instead of sending traffic on-premises when using pass-through authentication.
•\ By default, the Azure AD Connect sync server configures password hash synchronization between the on-premises domain and Azure AD, and the Azure AD service assumes that users authenticate by providing the same password that they use on-premises. The security policy of organization may prohibit synchronizing password hashes to the cloud. In this case, your organization should consider pass- through authentication.
The architecture has the following components:
•\ Azure AD tenant: An instance of Azure AD created by organization. It acts as a directory service for cloud applications by storing objects copied from the on-premises Active Directory and provides identity services.
•\ On-premises AD DS server: An on-premises directory and identity service. The AD DS directory can be synchronized with Azure AD to enable it to authenticate on-premises users.
•\ Azure AD Connect sync server: A computer that runs the Azure AD Connect sync service. This service synchronizes information held in the on-premises Active Directory to Azure AD. For example, if you provision or deprovision groups and users on-premises, these changes propagate to Azure AD.
•\ User authentication: By default, the Azure AD Connect sync server configures password hash synchronization between the on-premises domain and Azure AD, and the Azure AD service assumes that users authenticate by providing the same password that they use on-premises. For many organizations, this is appropriate,
but if your organization’s security policy prohibits synchronizing password hashes to the cloud, then you should consider pass-through authentication. Alternatively, you can configure Azure AD to use Active Directory Federation Services (AD FS) or a third-party federation provider to implement authentication and SSO rather than by using the password information held in the cloud.
