Plan a Host Pool Architecture and Recommendations for Resource Groups, Subscriptions, and Management Groups
We’ll cover several topics in this section.
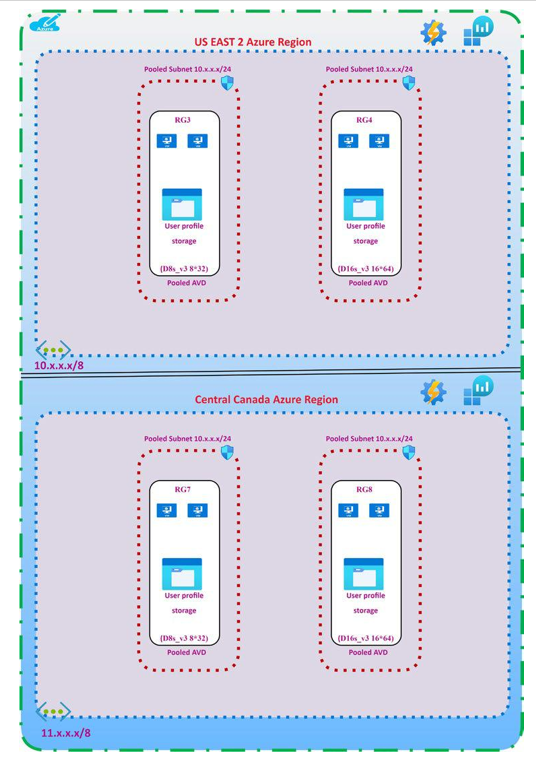
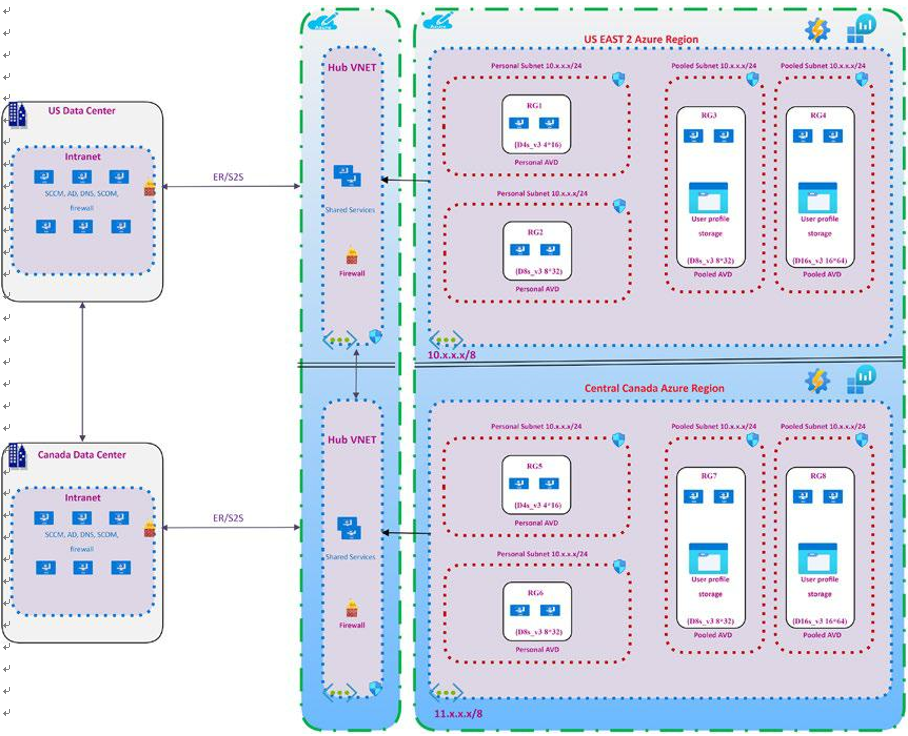
What Are Host Pools?
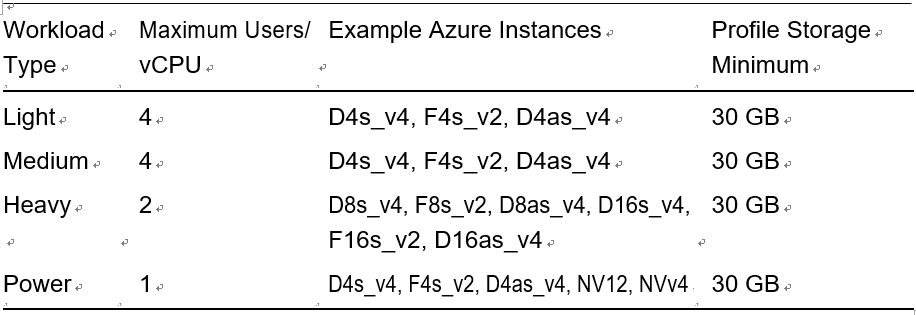
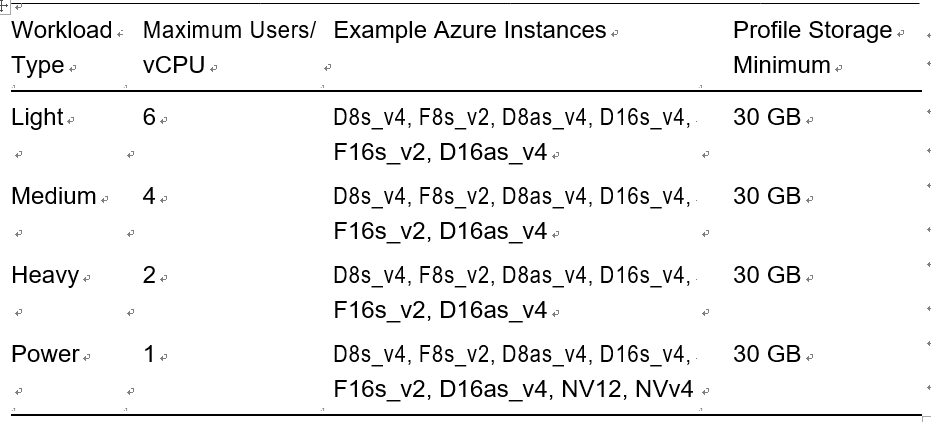
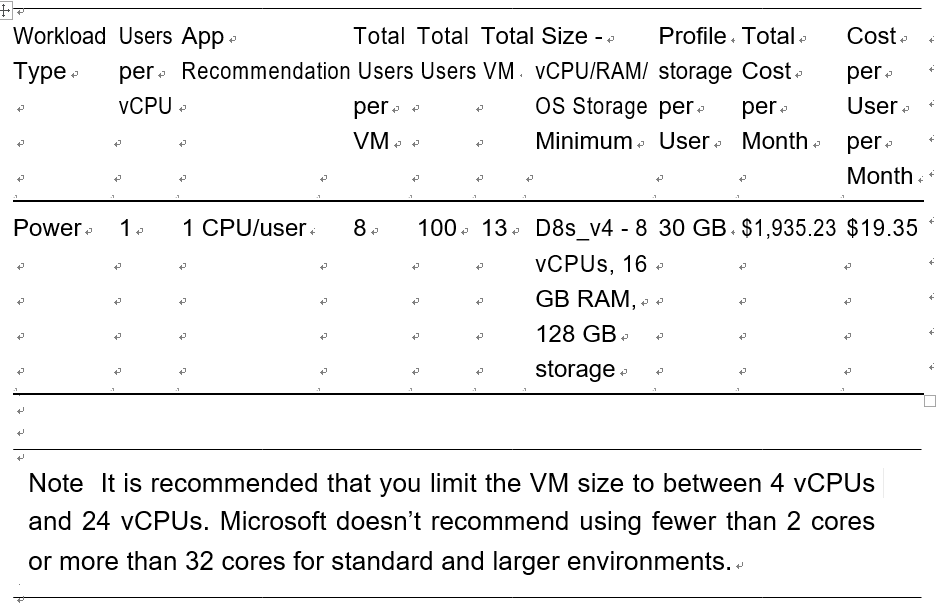
A host pool is a collection of Azure virtual machines with the same configuration. An Azure VM can be registered to Azure Virtual Desktop as session hosts when you run the Azure Virtual Desktop agent on the Azure VM. All session host virtual machines in a host pool should be sourced from the same image for a consistent user experience.
A host pool can be one of two types.
•\ Personal, where each user gets assigned to an individual session host.
•\ Pooled, where session hosts can accept connections from any user authorized to an app group within the host pool
You can set additional properties on the host pool to change its load-balancing behavior and the number of sessions each session host can take. You control the resources published to users through app groups. Refer to the “Configure host pool settings” section in Chapter 8 for a detail hostpool configuration.
What Are App Groups?
An app group is a logical grouping of applications installed on session hosts in the host pool. An app group can be one of two types.
•\ RemoteApp: Users access RemoteApp (a single application like Word or Excel) to individually publish to the app group. To publish to RemoteApp, you must create a RemoteApp app group. You can create multiple RemoteApp app groups to accommodate different worker scenarios. Different RemoteApp app groups can also contain overlapping RemoteApp instances.
•\ Desktop: Users access the full desktop. By default, a desktop app group is automatically created whenever you create a host pool. You can’t create another desktop app group in the host pool while a default desktop app group exists, but you can delete the default desktop group and create new one with a different name or use PowerShell/ARM to create a desktop group as per the naming standards you want.
To publish resources to users, you must assign them to app groups. When assigning users to app groups, consider the following:
•\ A user can be assigned to both a desktop app group and a RemoteApp app group in the same host pool. However, users can’t launch both types of app groups at the same time in a single session.
•\ A user can be assigned to multiple app groups within the same host pool, and their feed will be an accumulation of both app groups.